Discover the fundamentals of currency exchange rates in this informational post. Understand the factors that influence rates and the types of exchange rate systems. Gain the knowledge to navigate international currency conversions with confidence.
Author: Admin

The Benefits of Using Organic Makeup
Discover the numerous advantages of using organic makeup, from sustainable ingredients to eco-friendly packaging. Say goodbye to harsh chemicals and hello to a healthier, radiant complexion.

The Art of Mahjong: Mastering the Tiles
Discover the art of Mahjong and master its tiles. Explore its history, rules, different types of tiles, and strategies to become a Mahjong master.
How to Obtain a Massage Therapy Certification
Learn how to obtain a massage therapy certification and start a rewarding career. Get valuable insights and tips on the certification process.

Building a Strong Closeness with Your Spouse
Building a strong closeness with your spouse is essential for a healthy marriage. Learn practical strategies and mindset shifts for a lifetime of happiness and intimacy.

The Importance of Stock Market 윈조이머니상 추천 Research
Discover the importance of stock market research. Gain insights into market trends, risks, and opportunities. Make informed decisions to maximize your returns.

주식 투자의 기초 이해
주식 투자의 기초 이해 | 주식 투자의 중요성과 자본을 통한 수익 창출, 투자의 기본 원리, 주식 종류와 시장 동향에 대한 이해. 성공적인 전략과 신뢰성, 관련 정보와 매매 전략, 주식 분석 및 보유 기간, 주식 시장의 주요 인사이트에 대해 알아봅니다.
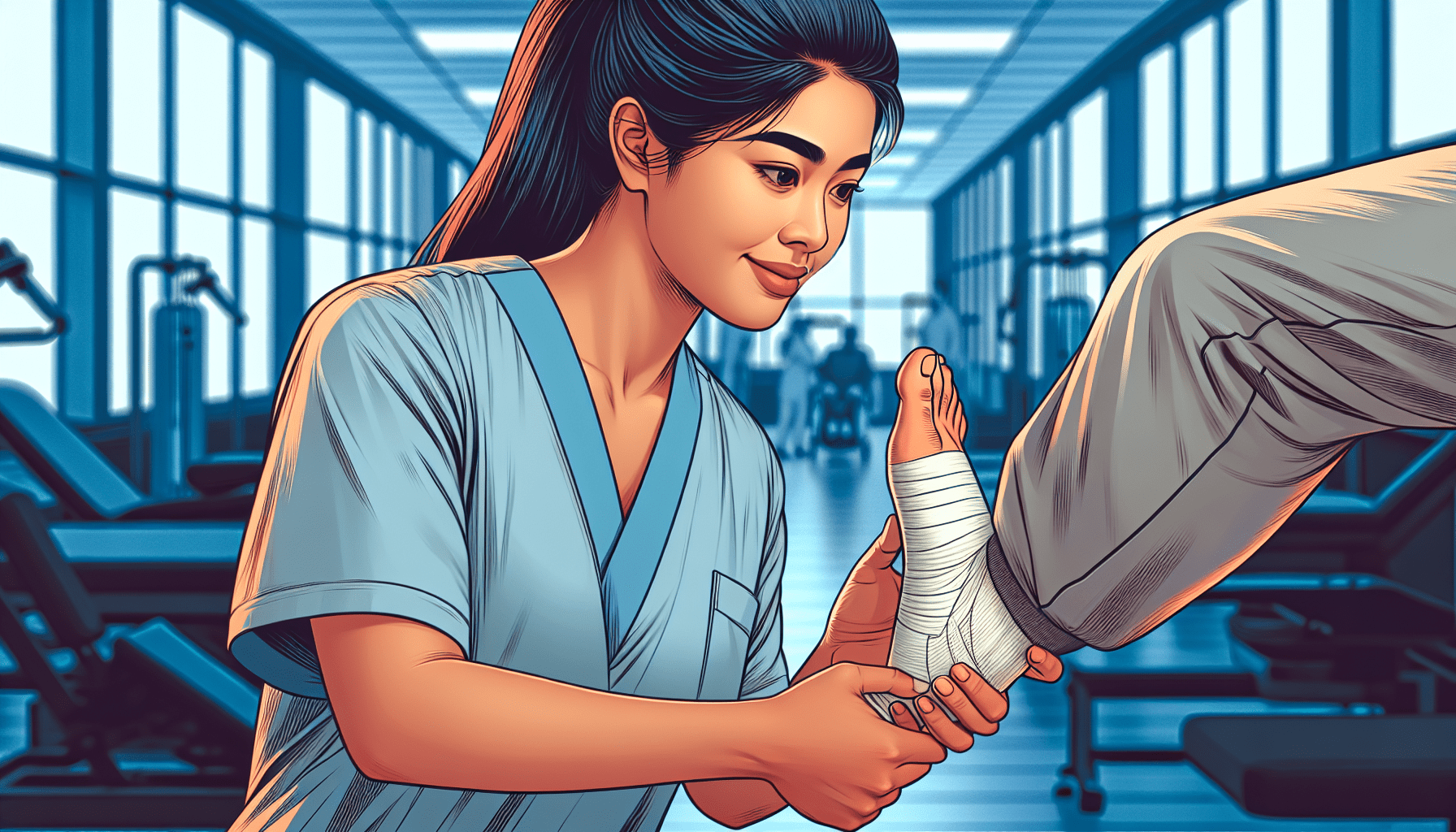
Shaping Futures: The Impact of Sanji University’s Physical Therapy Department
Discover the transformative impact of Sanji University’s Physical Therapy Department in shaping a brighter future. Explore their cutting-edge research, state-of-the-art facilities, and dedicated professionals advancing the field of physical therapy.

Exploring Gaming Tourism
Are you ready to embark on an exciting journey that fuses the exhilaration of gaming with the thrill of travel? Look no further than the fascinating world of gaming tourism. This captivating form of t…

Exploring the Mini-games and Side Activities
Embark on an exciting journey into the captivating world of mini-games and side activities. Discover hidden gems that enhance your gaming experience.
